Are You Evaluating All Necessary Attack Vectors To Protect Your Entire Business Ecosystem?

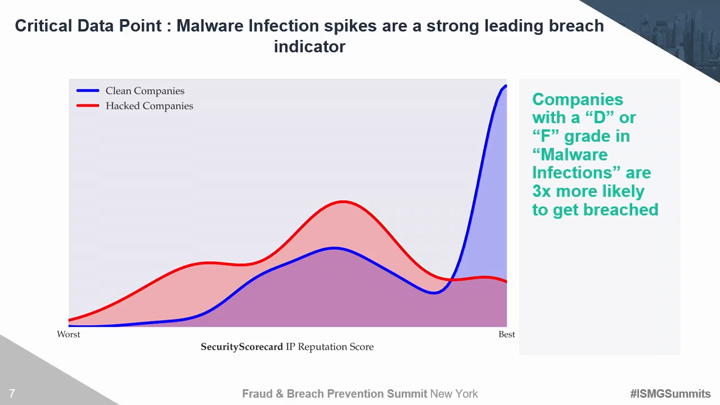
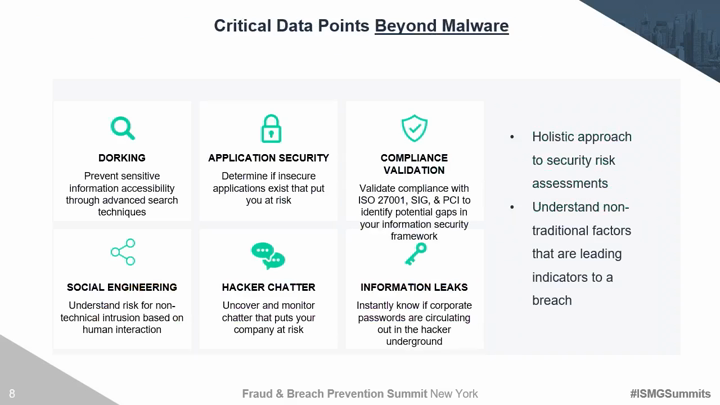
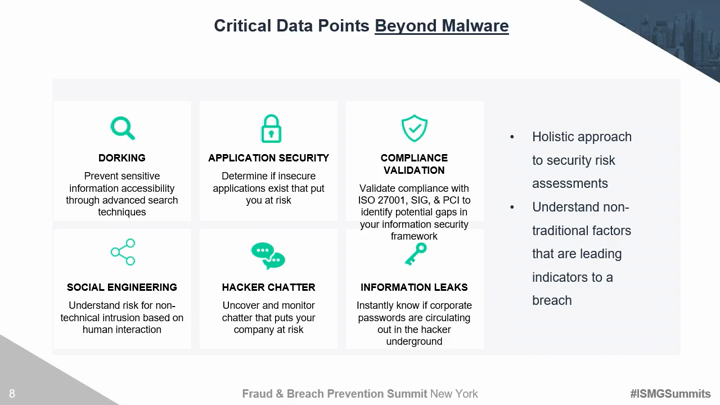
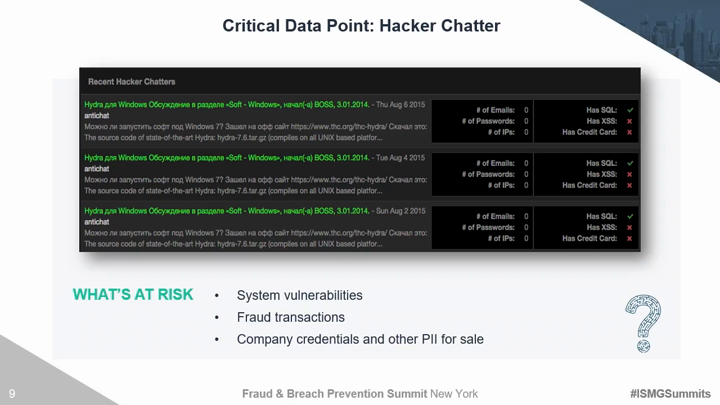
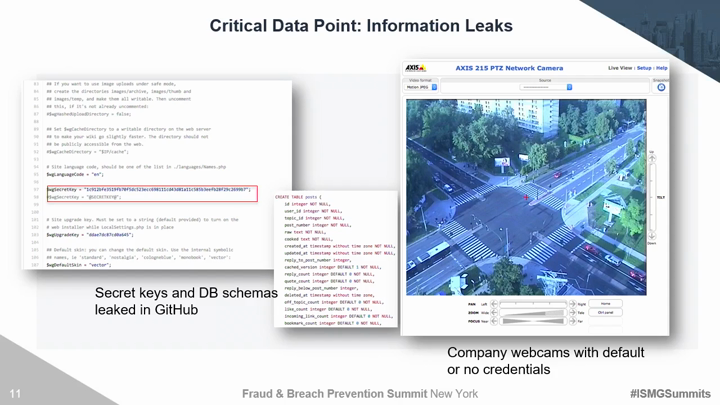
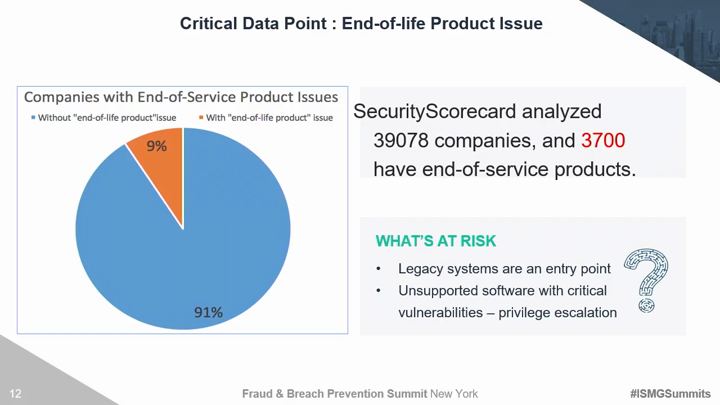
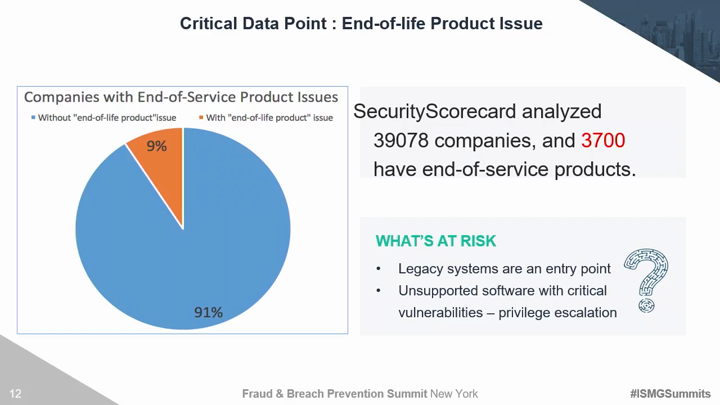
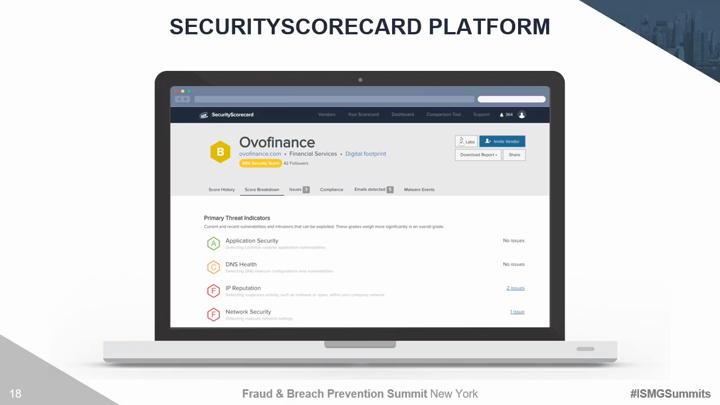
Traditional third party risk management solutions and techniques are no longer effective. Organizations must move beyond trust based exercises and canned IT infrastructure evidence to evaluate areas of compromise. There are several discrete security areas that must be continuously evaluated for vendors, partners, and yourself to understand the true risk of a breach. Critical risk factors include the ability to monitor hacker chatter on the deep dark web, employee susceptibility to social engineering, and the overall security maturity of your 3rd and 4th party vendors. This session will introduce security technologies and techniques to:
See Also: Research Survey Analysis: Securing Your Third-Party Supply Chain in 2024
- Holistically monitor and evaluate critical attack vectors across your entire business ecosystem;
- Understand the security factors that put you most at risk, and how to reduce your exposure;
- Move beyond traditional onsite risk assessments and point- in-time penetration tests to gain real-time context of your third party environment;
- Progress past 3rd party risk to 4th, and 5th party assessments and beyond;
- Prioritize policy checks and due diligence resources based on advanced risk scoring;
Additional Summit Insight:
Hear from more industry influencers, earn CPE credits, and network with leaders of technology at our global events. Learn more at our Fraud & Breach Prevention Events site.